11# Mayhem for API: Example CI integration
22
3- [ ![ Mayhem for API] ( https://mayhem4api.forallsecure.com/static/media/ logo.f8497128 .svg )] ( http://mayhem4api.forallsecure.com/signup )
3+ [ ![ Mayhem for API] ( https://mayhem4api.forallsecure.com/downloads/img/mapi- logo-full-color .svg )] ( http://mayhem4api.forallsecure.com/signup )
44
55## About Mayhem for API
66
@@ -17,8 +17,7 @@ our job easier!
1717and PRs. We make it easy, and provide results right in your PRs where
1818you want them. Adding Mayhem for API to a DevOps pipeline is easy.
1919
20- Want to try it? Start a [ 30-day free
21- trial] ( http://mayhem4api.forallsecure.com/signup ) .
20+ Want to try it? [ Sign up for free] ( http://mayhem4api.forallsecure.com/signup ) !
2221
2322## Example GitHub Actions Integration
2423
@@ -28,19 +27,12 @@ for API.
2827### Starting a Mayhem for API scan in Github Actions
2928
3029To scan your API with Mayhem for API in CI, you need to:
31- 1 ) Download the Mayhem for API CLI
32- 2 ) Start your API
33- 3 ) Start the Mayhem for API scan
30+ 1 ) Start your API
31+ 2 ) Start the Mayhem for API scan
3432
3533In GitHub actions, those steps translate to:
3634
3735``` yaml
38- # Download Mayhem for API CLI for linux (also available for windows and Mac
39- - name : Download API fuzzer CLI
40- run : |
41- curl -s -LO https://mayhem4api.forallsecure.com/downloads/cli/latest/linux-musl/mapi
42- chmod +x ./mapi
43-
4436 # Run API in test mode. We configured test mode to output stacktraces in
4537 # the error responses to improve the output of Mayhem for API.
4638 - name : Run API
@@ -49,51 +41,74 @@ In GitHub actions, those steps translate to:
4941 run : uvicorn src.main:app &
5042
5143 # Run Mayhem for API
52- - name : Mayhem for API Scan
53- env :
54- MAPI_TOKEN : ${{ secrets.MAPI_TOKEN }}
55- run : ./mapi run fastapi 10 --url http://localhost:8000/ --sarif results.sarif --html results.html http://localhost:8000/openapi.json || true
44+ - name : Run Mayhem for API to check for vulnerabilities
45+ uses : ForAllSecure/mapi-action@v1
46+ with :
47+ mapi-token : ${{ secrets.MAPI_TOKEN }}
48+ api-url : http://localhost:8000
49+ api-spec : http://localhost:8000/openapi.json
5650` ` `
5751
5852This repo contains a [full example](.github/workflows/mapi.yml) for
5953reference.
6054
61- ## Results
55+ # Reports
6256
63- Mayhem for API outputs reports in multiple formats (jUnit, SARIF, HTML).
64- In this instance, we requested a HTML report and a SARIF report.
57+ Mayhem for API generate reports when you pass ` sarif-report` or
58+ ` html-report` to the input. Make sure to pass `continue-on-error` to the
59+ Mayhem for API step if you want to process the reports in follow-up
60+ steps.
6561
66- ### Artifact HTML Report
62+ # # Artifact HTML Report
6763
6864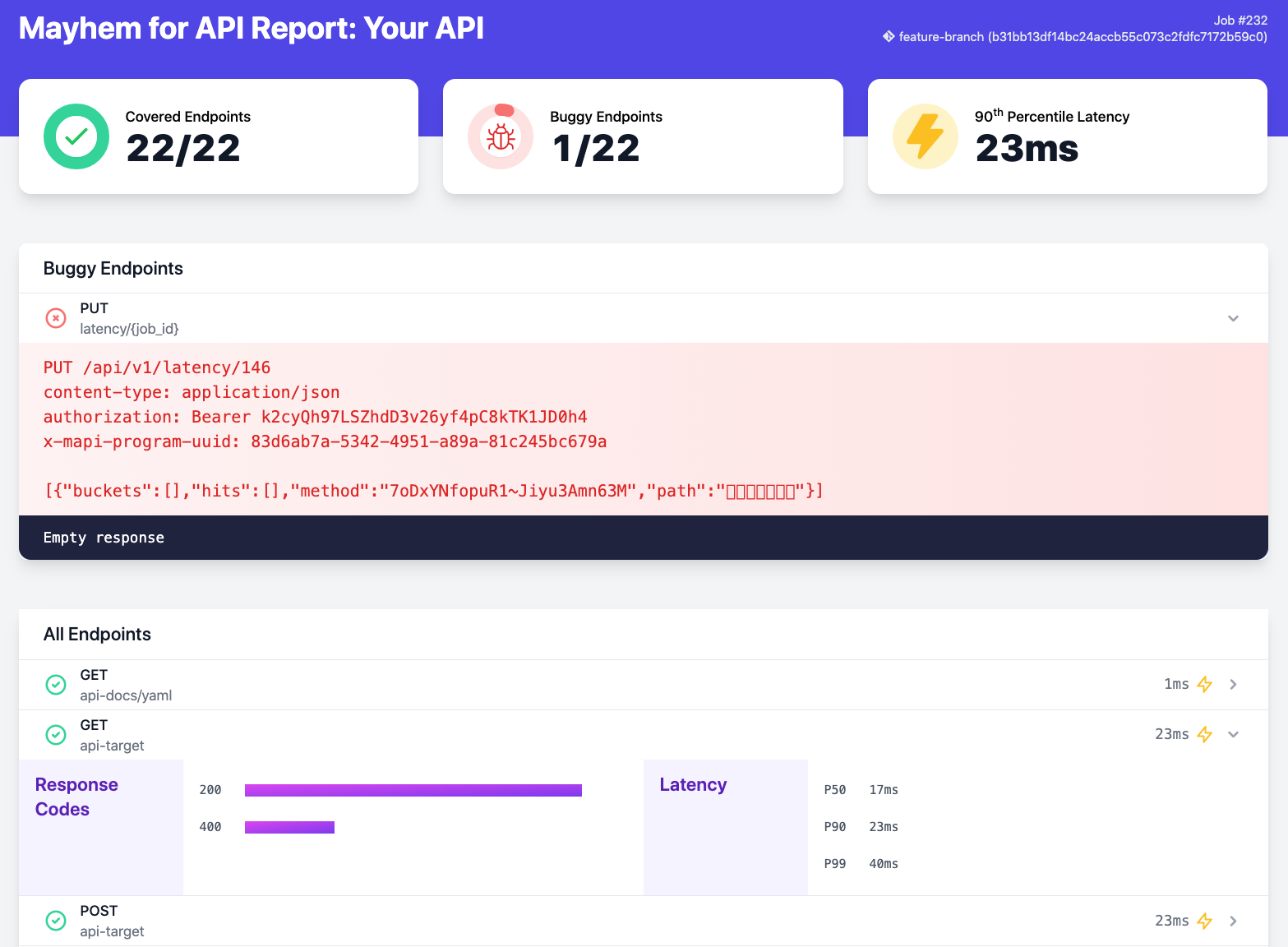
6965
7066To artifact the report in your build, add this step to your pipeline :
7167
7268` ` ` yaml
73- # Archive HTML report
74- - name : Archive code coverage results
75- uses : actions/upload-artifact@v2
76- with :
77- name : mapi-report
78- path : results.html
69+ - name: Run Mayhem for API to check for vulnerabilities
70+ uses: ForAllSecure/mapi-action@v1
71+ continue-on-error: true
72+ with:
73+ mapi-token: ${{ secrets.MAPI_TOKEN }}
74+ api-url: http://localhost:8000 # <- update this
75+ api-spec: your-openapi-spec-or-postman-collection.json # <- update this
76+ html-report: mapi.html
77+
78+ # Archive HTML report
79+ - name: Archive Mayhem for API report
80+ uses: actions/upload-artifact@v2
81+ with:
82+ name: mapi-report
83+ path: mapi.html
7984` ` `
8085
81- ## Upload SARIF
86+ # # GitHub Code Scanning support
8287
8388
8590
86- Uploading SARIF to GitHub allows you to see any issue found by Mayhem
87- for API right on your PR! This currently requires you to have a GitHub
88- Enterprise Plan or have a public repository. To upload the SARIF report,
89- add this step to your pipeline:
91+ Uploading SARIF reports to GitHub allows you to see any issue found by
92+ Mayhem for API right on your PR, as well as in the "Security" tab of
93+ your repository. This currently requires you to have a GitHub Enterprise
94+ Plan or have a public repository. To upload the SARIF report, add this
95+ step to your pipeline :
9096
9197` ` ` yaml
92- # Upload SARIF file (only available on public repos or github enterprise)
93- - name : Upload SARIF file
94- uses : github/codeql-action/upload-sarif@v1
95- with :
96- sarif_file : results.sarif
98+ - name: Run Mayhem for API to check for vulnerabilities
99+ uses: ForAllSecure/mapi-action@v1
100+ continue-on-error: true
101+ with:
102+ mapi-token: ${{ secrets.MAPI_TOKEN }}
103+ api-url: http://localhost:8000 # <- update this
104+ api-spec: your-openapi-spec-or-postman-collection.json # <- update this
105+ sarif-report: mapi.sarif
106+
107+ # Upload SARIF file (only available on public repos or github enterprise)
108+ - name: Upload SARIF file
109+ uses: github/codeql-action/upload-sarif@v1
110+ with:
111+ sarif_file: mapi.sarif
97112` ` `
98113
99114If your API server sends back stacktraces in the 500 Internal Server
0 commit comments